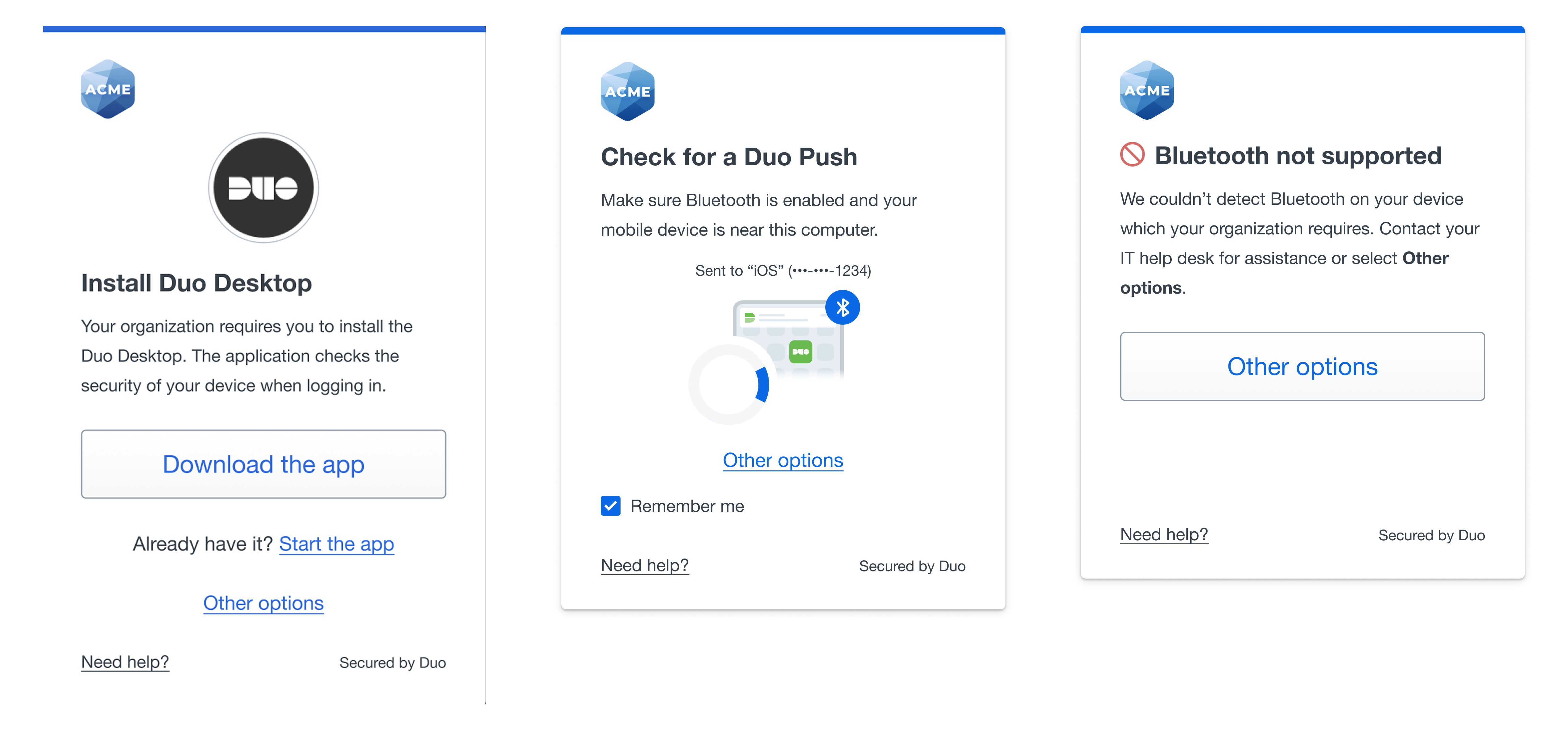
Duo Mobile Push - Bluetooth
Duo Security, now part of Cisco, offers multi-factor authentication, boosting digital security by verifying identities and preventing unauthorized access.
.png)
Overview
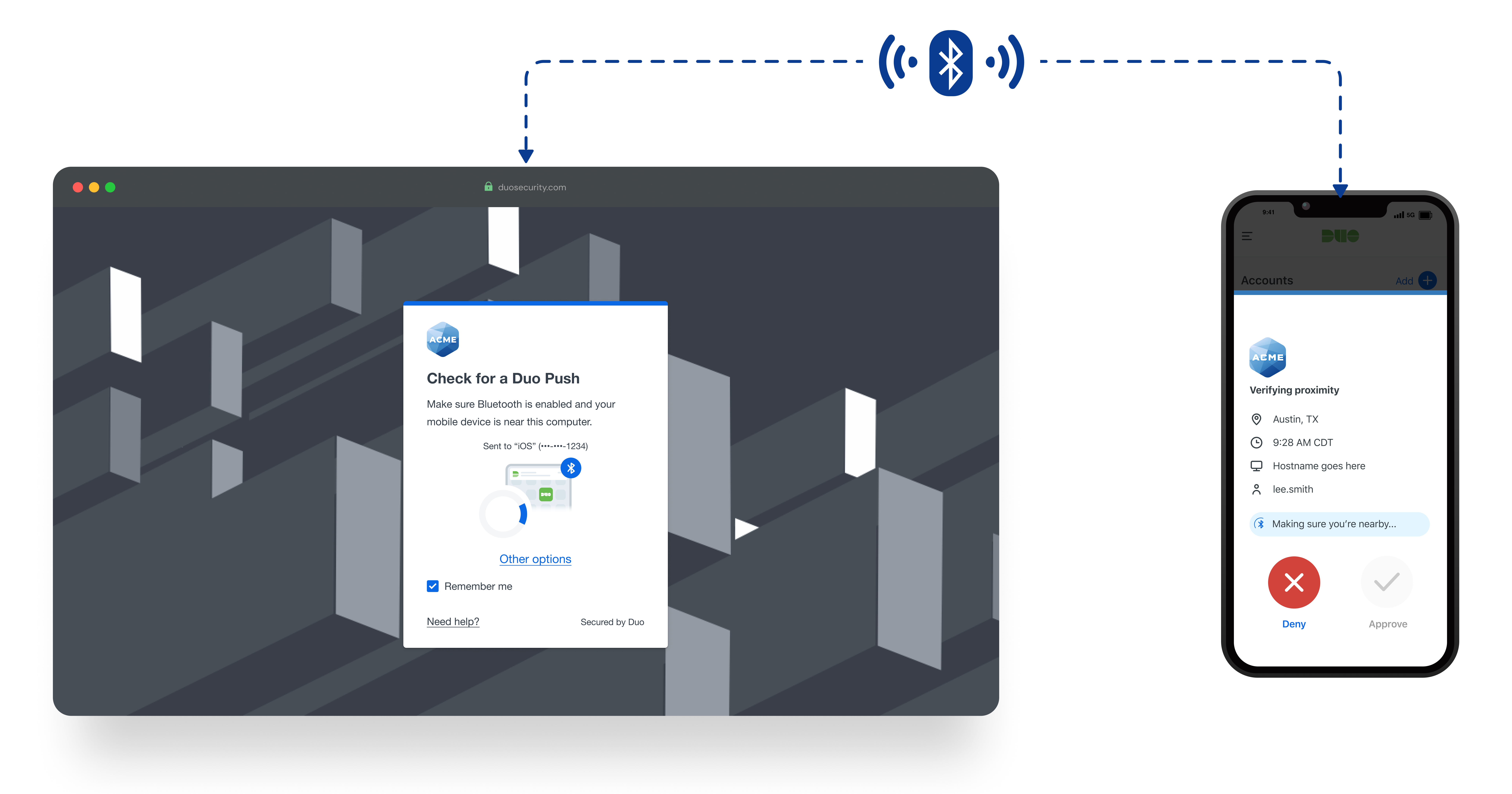
Bluetooth Duo Push is an enhanced authentication method that uses Bluetooth technology to confirm a user’s phone is physically near their computer during login. It builds on the familiar Duo Push experience and adds a layer of security behind the scenes without adding friction for the user.

Problem:
As phishing attacks become more advanced, organizations need stronger protection during login but many cannot afford or manage hardware-based security keys. Existing backup methods like entering a code manually leave room for human error and potential remote attacks.
Solution:
Bluetooth Duo Push verifies proximity automatically using Bluetooth and blocks login attempts when the phone is not nearby. It removes the need for backup code entry and keeps the experience simple with just one tap to log in. This approach provides strong phishing-resistant security without the cost or complexity of hardware tokens.
Key Results:
- The feature officially reached General Availability (GA) in June 2025, making it fully rolled out and ready for all customers.
- 1 month after GA, 187 customers generated approximately 32,000 authentications using Bluetooth-based Duo Push.
- As part of Duo’s efforts to phase out weaker authentication methods, phishing-resistant options increased from 19% to 27% of total authentications over the past year.
Project Challenges:
- Managing two major features built concurrently within a single project scope
- Supporting multiple active initiatives dependent on this feature
- Managing cross-platform complexities across iOS and Android, including capability differences and device-level limitations
Understand
To start off this project, we examined the internal processes, explored the product, and evaluated its existing state.
Iterative Design Across Release Stages
Duo Security’s release cycle moves from Private Preview for early technical validation, to Public Preview for usability and feedback, and finally to General Availability for full market release. The phased release approach at Duo Security made the design process iterative. We started with the smallest scope and gradually expanded, allowing the designs to evolve in each stage based on feedback and real-world usage.

Personas + Product Usage
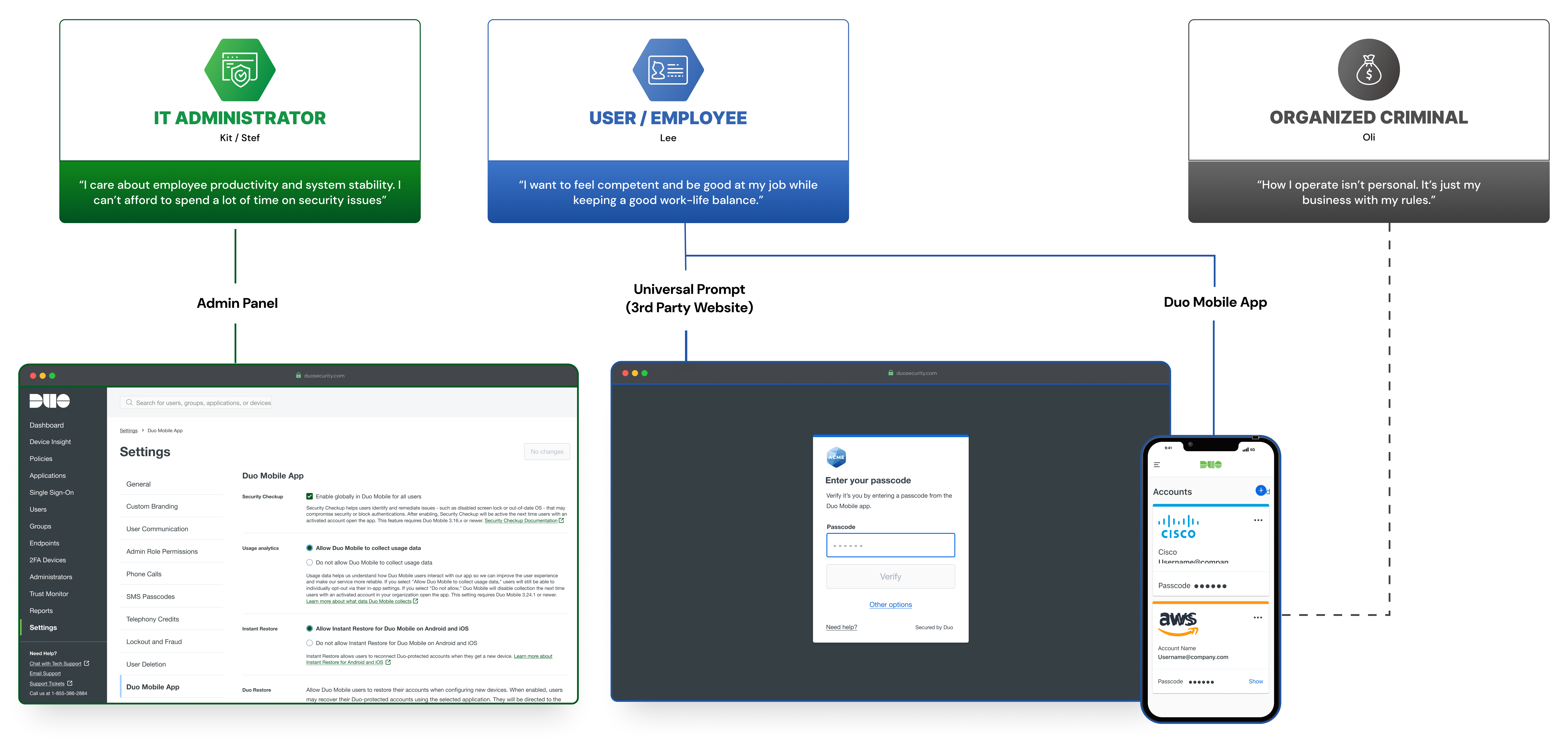
Out of 29 different personas, we focus on 3 key personas for this project and analyze which parts of the product each one uses.
- IT Administrator: Implement secure, phishing-resistant authentication methods that protect the organization without disrupting productivity.
- End User: Access my work apps quickly and with as little friction as possible.
- Organized Criminal/Attacker: Trick users into giving up credentials or bypass MFA to access protected systems.
Overview of Duo Push Variants
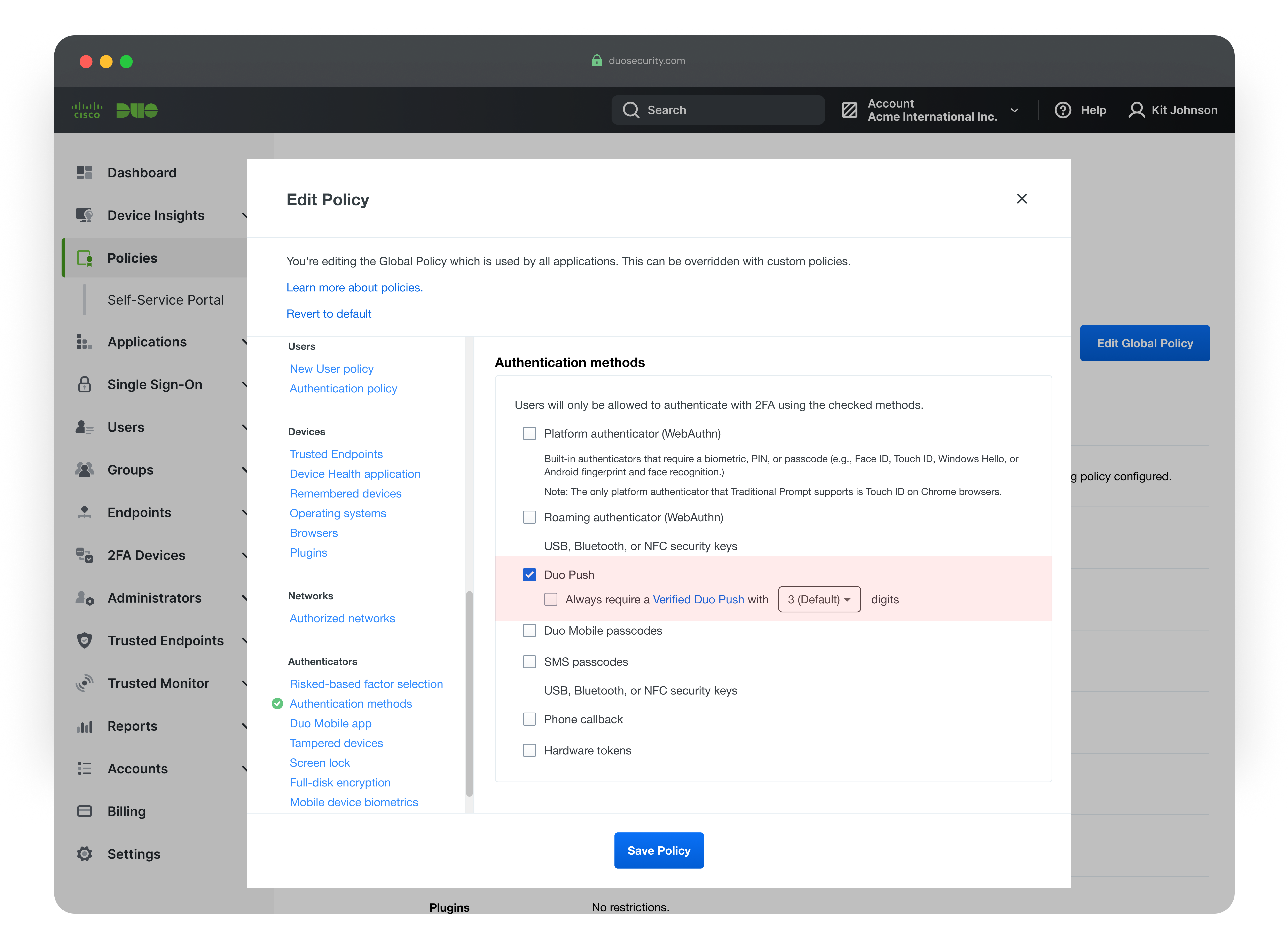
Duo offers multiple Push authentication options—standard Duo Push and Verified Duo Push (which requires users to enter a code shown on screen)—each providing different levels of phishing resistance and user interaction.
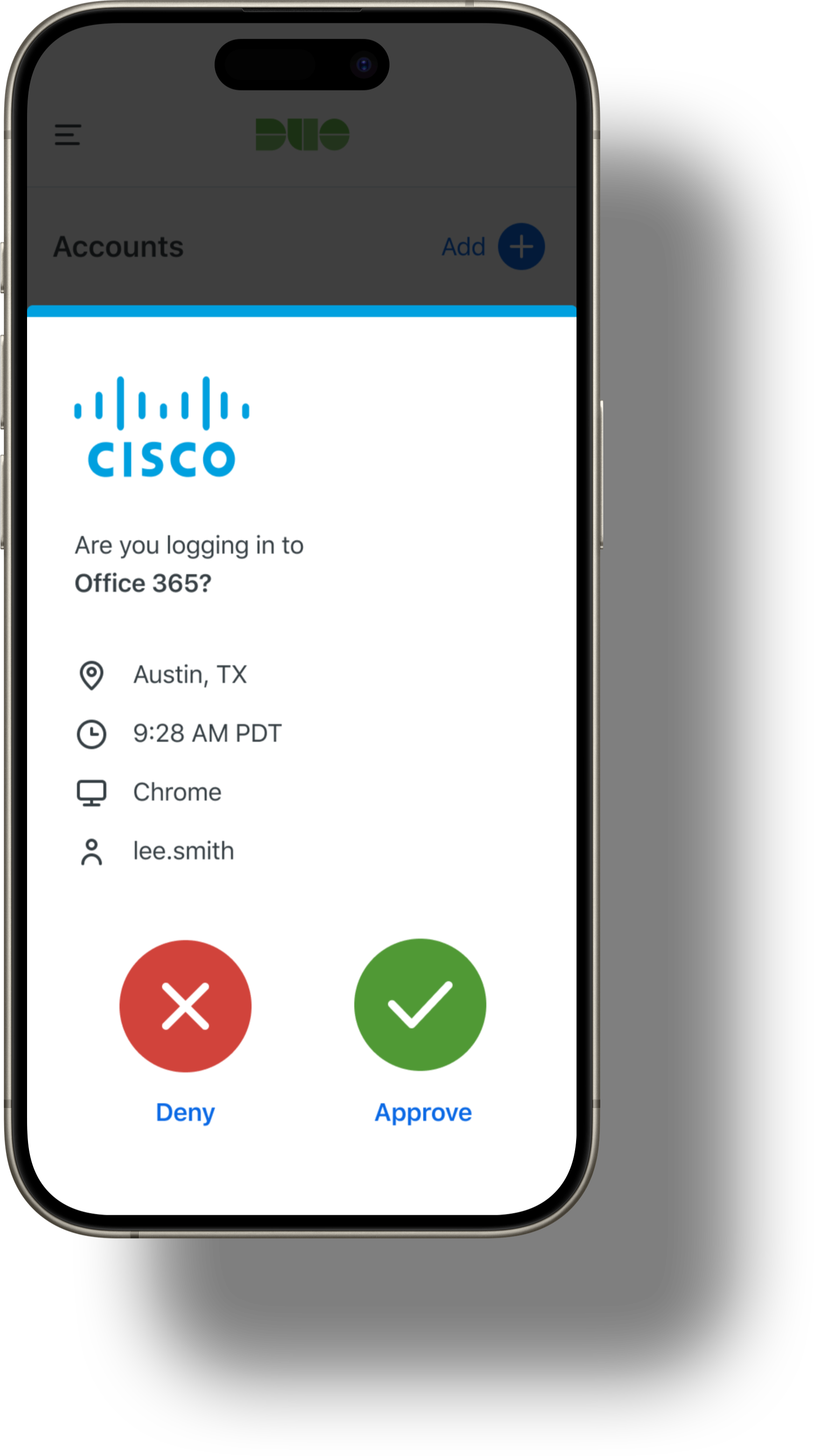
(1) Duo Push:
A two-factor authentication method where users receive a push notification on their mobile device upon login. They can approve or deny the request with a single tap, providing a quick and secure way to verify their identity.
Security properties:
- Confirms user identity through device possession.
- Protects against phishing by ensuring the request is legitimate.
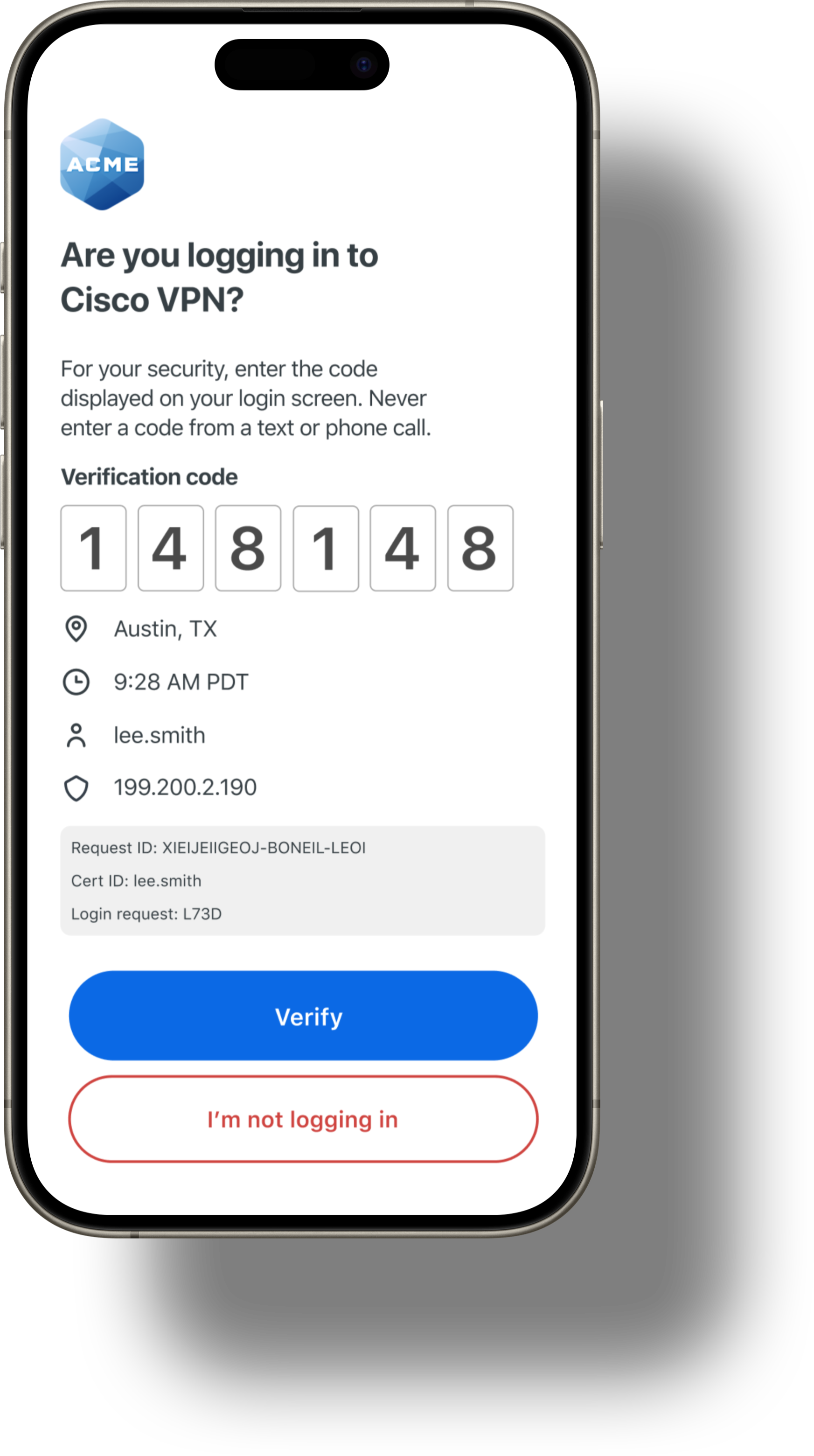
(2) Verified Duo Push:
Enhances Duo Push by requiring users to enter a verification code displayed on their login screen into the Duo Mobile app. This additional step mitigates push fatigue and accidental approvals.
Security properties:
- Adds an extra layer of verification, reducing the risk of unauthorized access.
- Helps prevent accidental or fraudulent approvals caused by “push fatigue” (repeated unsolicited push requests).
Setting Configuration
The current state shown here reflects how admins can configure Duo Mobile settings to allow either standard Duo Push or Verified Duo Push.
Phase 1
We kept the initial rollout lightweight to test core Bluetooth functionality and start gathering feedback on how customers use and respond to the feature.

Goals:
- Test core functionality with minimal lift to get early insights.
- Learn how customers use the feature and gather feedback for future improvements.
- Encourage customers to adopt stronger, phishing-resistant authentication methods.
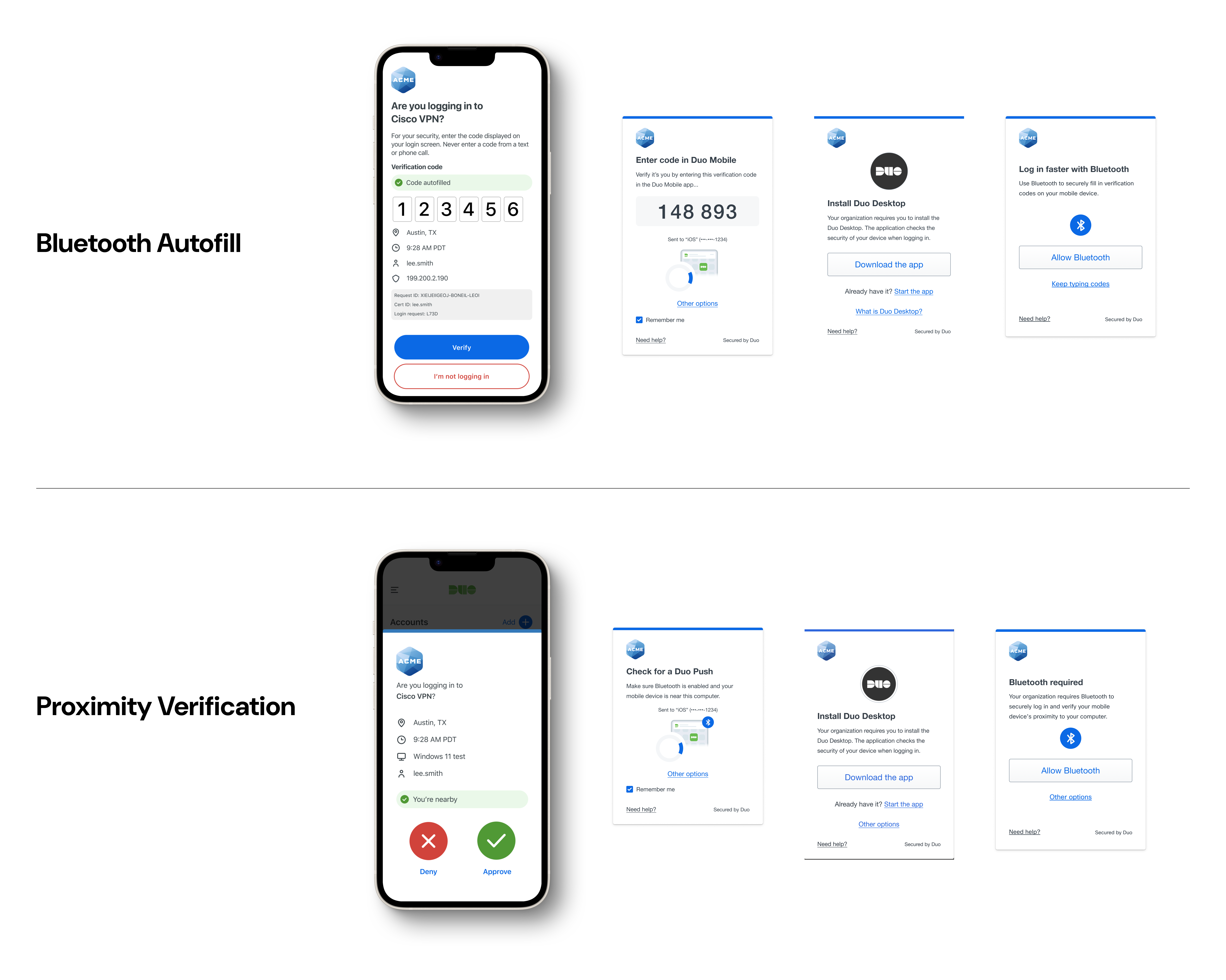
Bluetooth + Verified Push = Bluetooth Autofill
The existing Verified Duo Push experience was enhanced by adding a Bluetooth-based proximity check, accompanied by a visual spinner that indicates the system is verifying nearby devices. Checking for device proximity through Bluetooth adds an extra layer of security while enhancing the overall user experience by making authentication smoother and more seamless, helping increase our Verified Push adoption rates while maintaining stronger security than regular Duo Push.
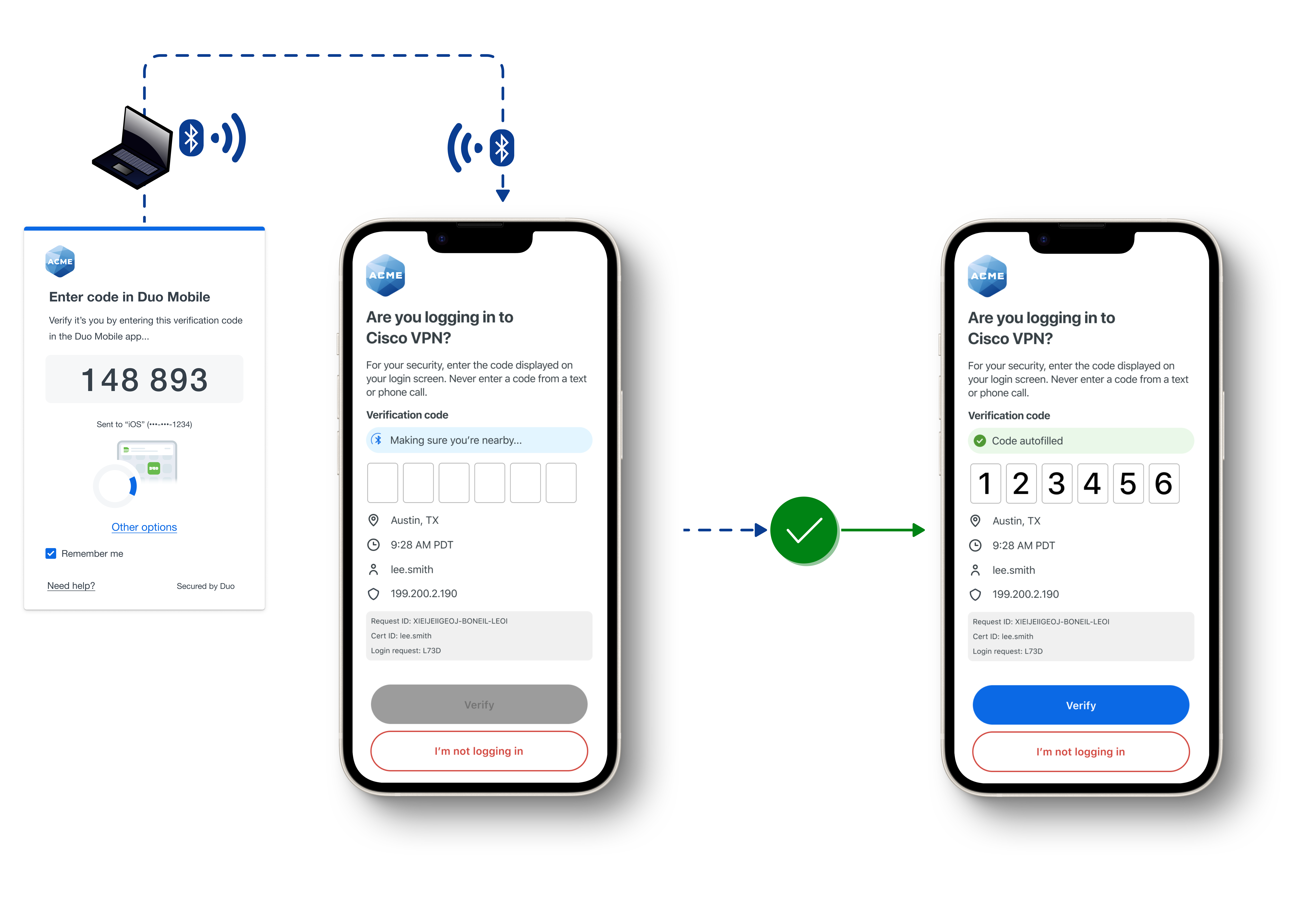
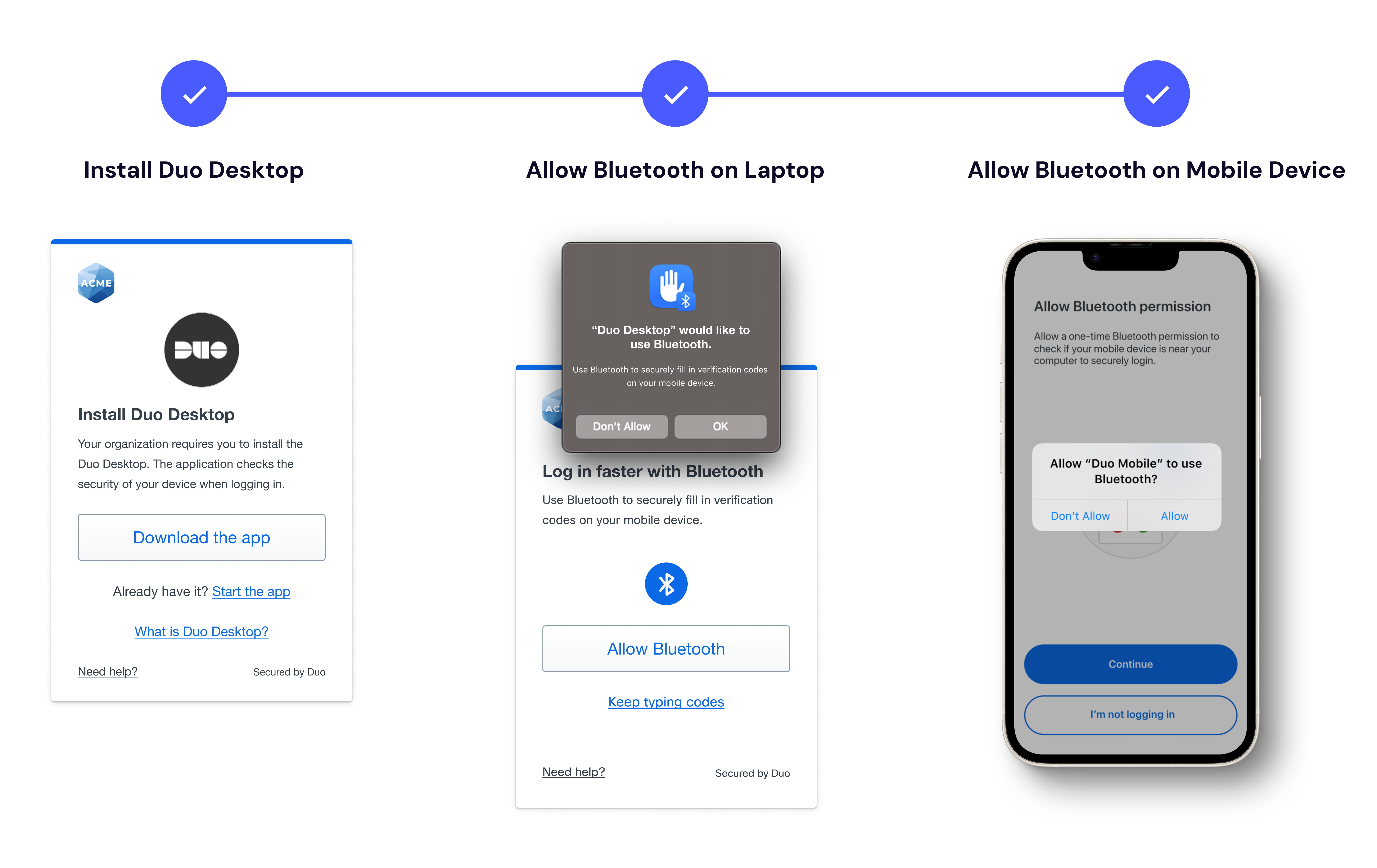
Device and Bluetooth Requirements
- Duo Desktop must be installed on the user’s device
- The first-time experience requests Bluetooth Low Energy (BLE) permissions on both laptop and mobile devices
- If there are any BLE issues or device limitations, users can continue authenticating by entering codes manually.
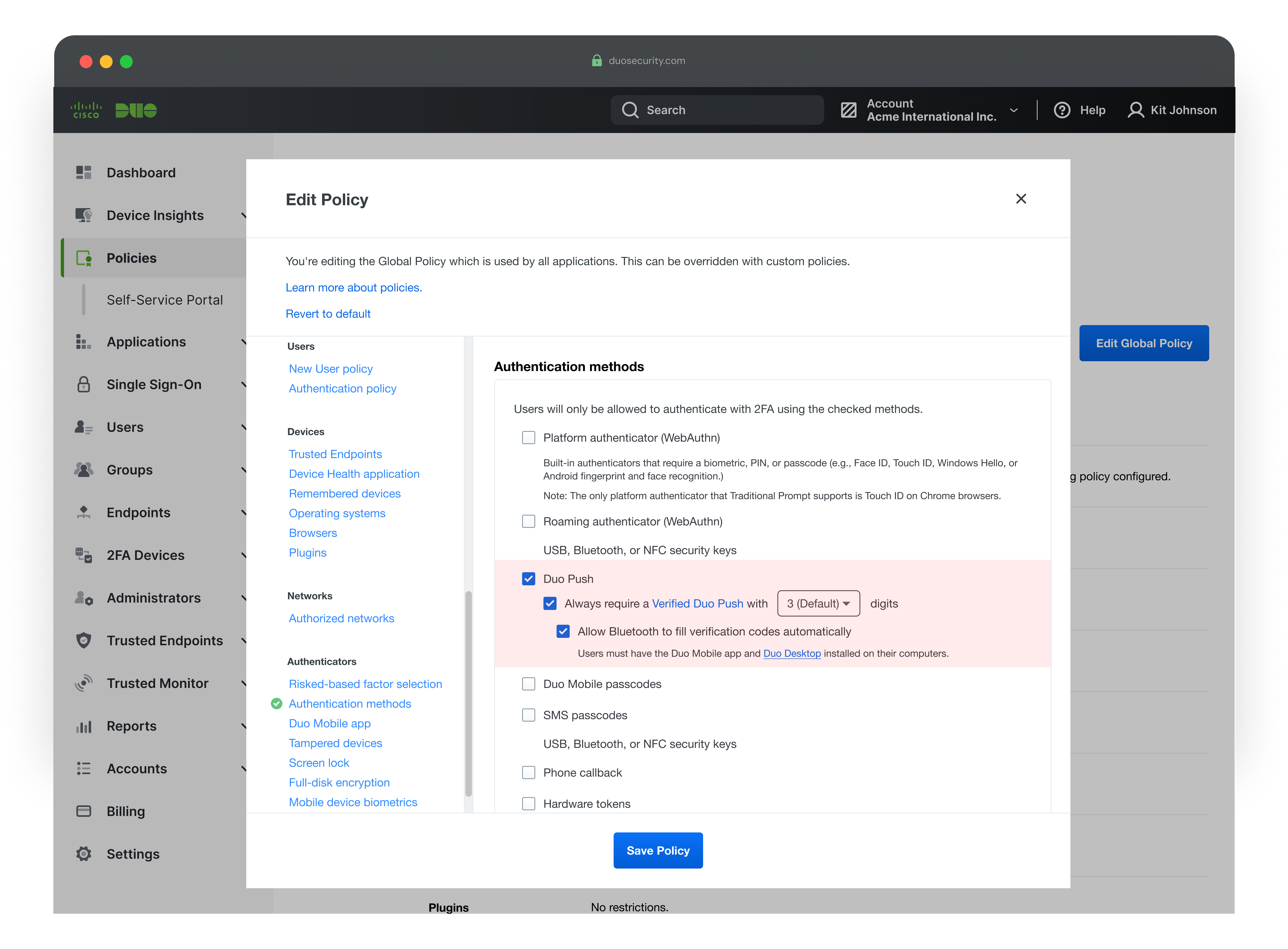
Settings Configuration
The settings configuration allows admins to enable Verified Duo Push, with a nested checkbox option to autofill the code using Bluetooth after a successful proximity check, giving control over both security and user experience.
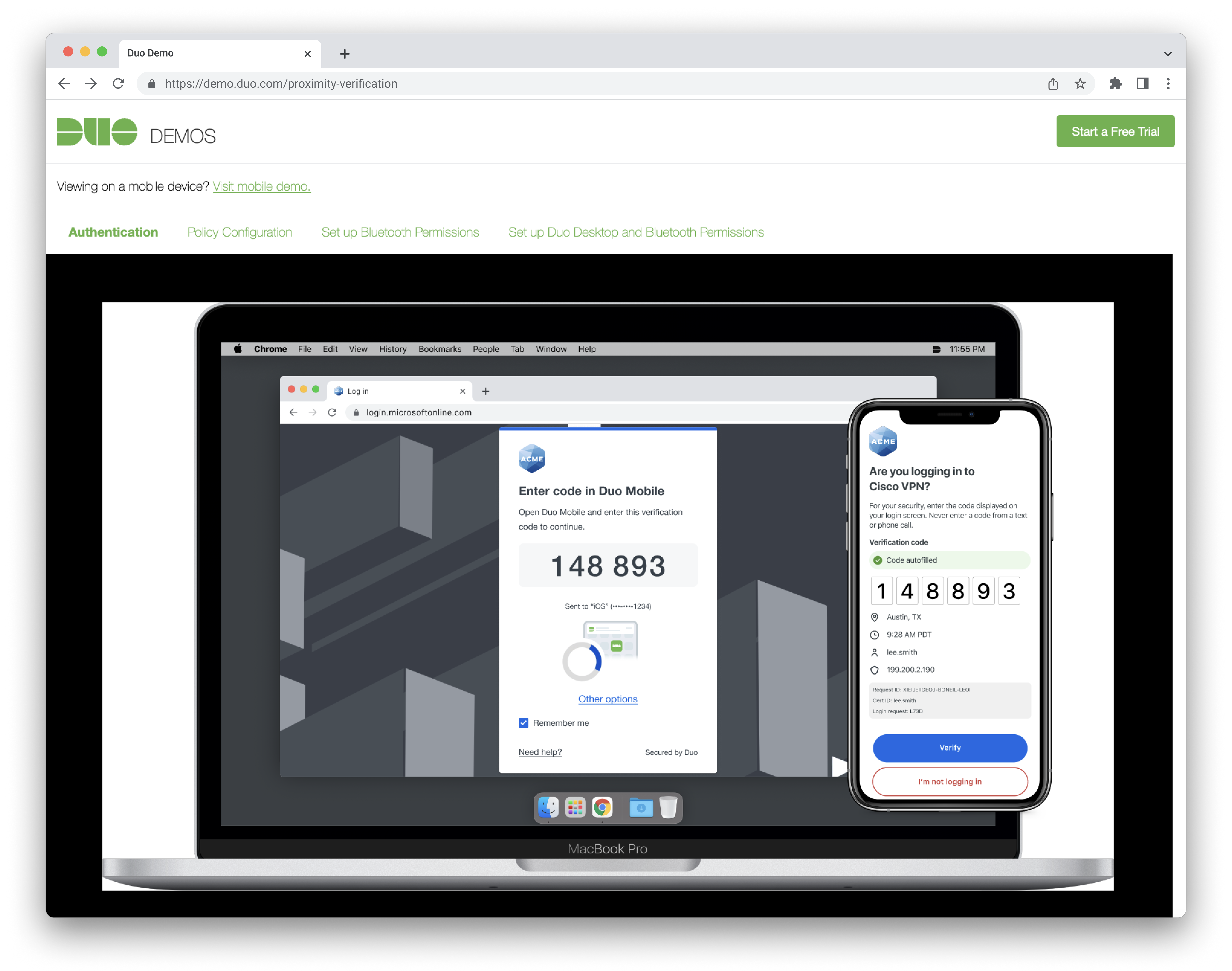
Prototype Flows:
- Authentication: Verified Duo Push with Bluetooth autofill
- Setup: Bluetooth Permissions
- Setup: Duo Desktop & Bluetooth Permissions
- Admin: Policy Configuration
Customer Insights:
- Tested by 7 customers over an 8-week period.
- Feedback was overall very positive especailly after working through setup & bluetooth related issues
- Improvement needed: Ability to filter authentication logs and reports, with Bluetooth-related events clearly marked.
"It was seamless. It was nice, instead of entering the numbers manually. So far I would say it's more convenient, and I am liking it."
"We would roll this out to everyone. I see it as a security benefit."
Phase 2:
We took the next step by introducing a stricter, phishing-resistant authentication option to raise the security baseline and learn how customers respond to more advanced protection methods.

Goals:
- Introduce a stronger, phishing-resistant option to elevate security
- Validate that the Bluetooth feature performs as intended
- Understand how customers respond to increased authentication requirements.
Bluetooth + Duo Push = Proximity Verification
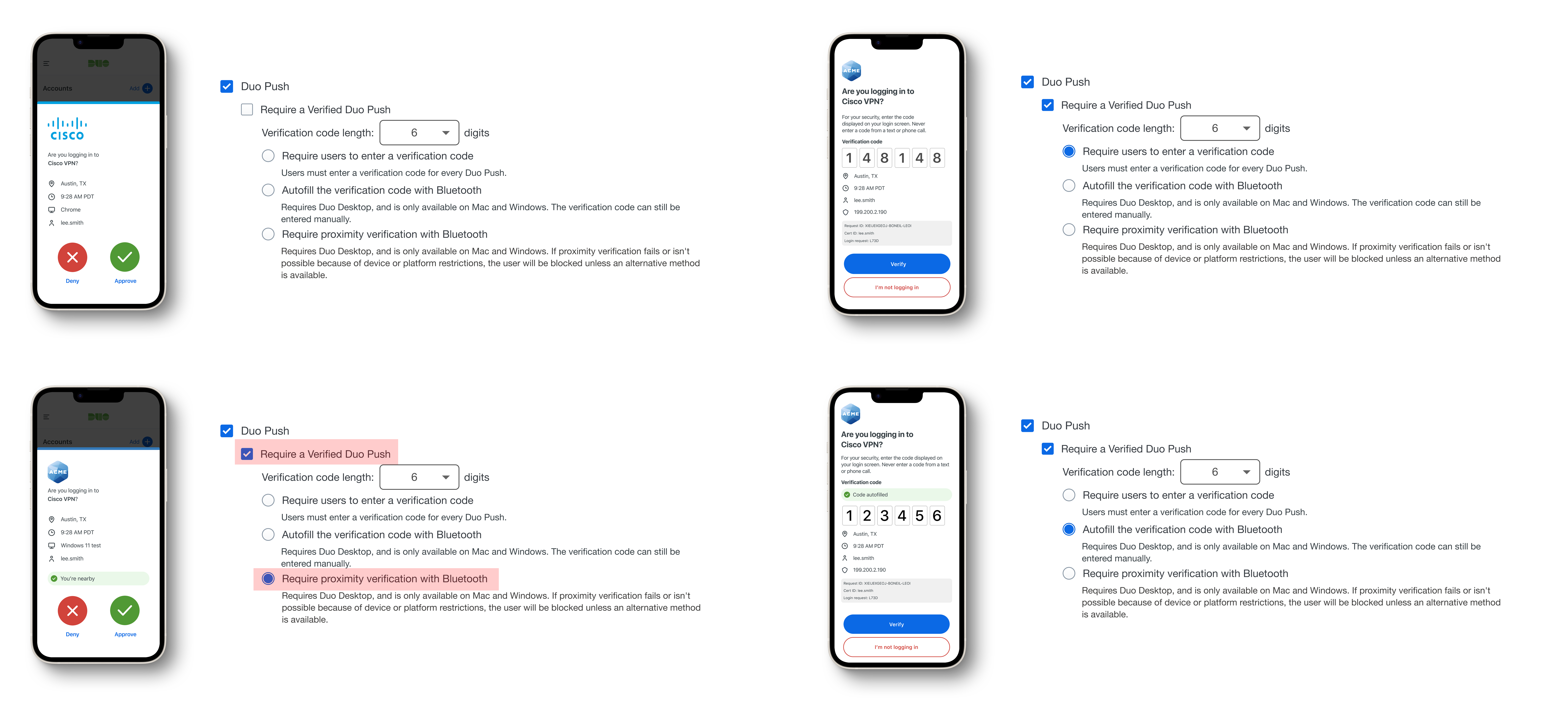
Proximity Verification builds on the same Bluetooth-based proximity check used in Verified Duo Push, but takes a stricter and more phishing-resistant approach. The user still sees the standard Duo Push screen, but the 6-digit code is hidden in the background. There is no option to type the code, so authentication can only complete if the devices are physically near each other. This adds stronger security while keeping the user experience familiar and seamless.
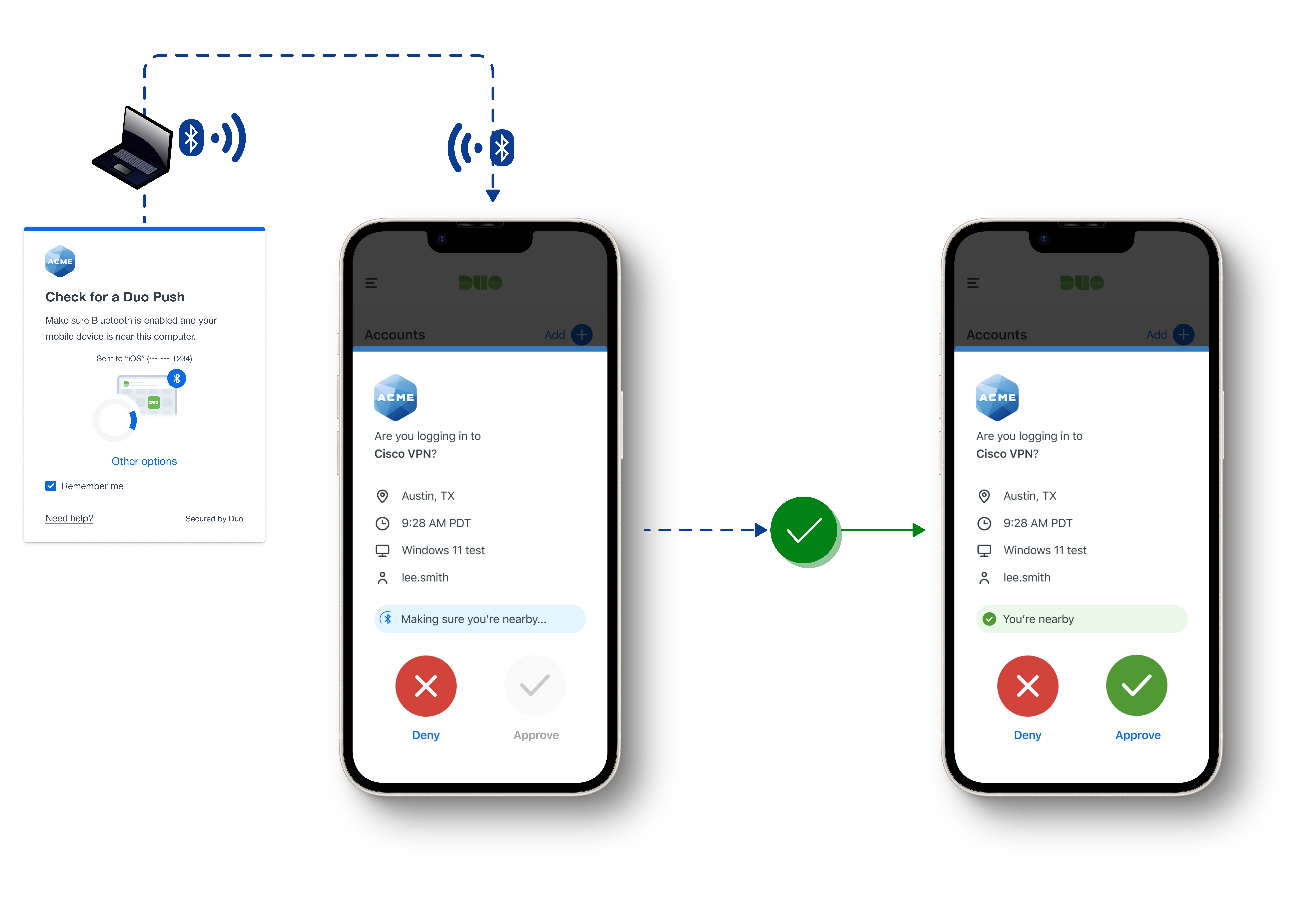
Key Differences Between Bluetooth Autofill and Proximity Verification
- Each method uses a different prompt screens in the Duo Universal Prompt
- Bluetooth Autofill allows users to see and enter a 6-digit code; Proximity Verification hides the code and requires close device proximity
- Users exit the flow differently when Bluetooth fails (Autofill falls back to manual code entry; Proximity Verification may block access)
- Proximity Verification enforces a higher level of security by removing fallback options like code typing
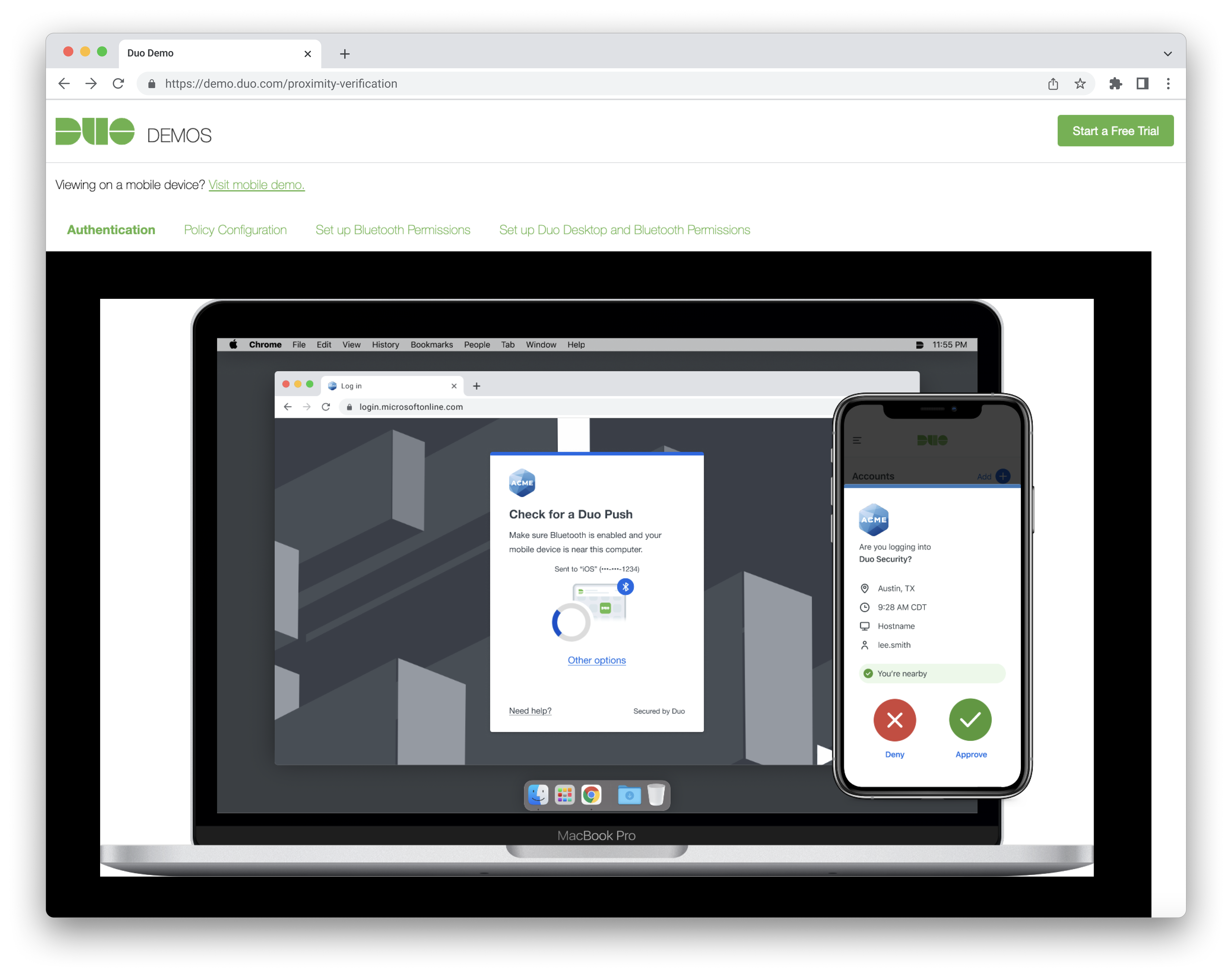
Prototype Flows:
- Authentication: Proximity Verification
- Setup: Bluetooth Permissions
- Setup: Duo Desktop & Bluetooth Permissions
- Admin: Policy Configuration
Updated Settings Configuration
The settings for Verified Duo Push now include three radio buttons, giving admins control over the level of authentication security. Each option increases security as you move down the list.
- Default option: Displays a 6-digit code for users to enter manually.
- Bluetooth autofill option: Uses Bluetooth to check proximity and autofills the code, showing the “Approve” screen only when devices are nearby.
- Proximity Verification: Requires close proximity but hides the code completely, offering the most phishing-resistant experience.
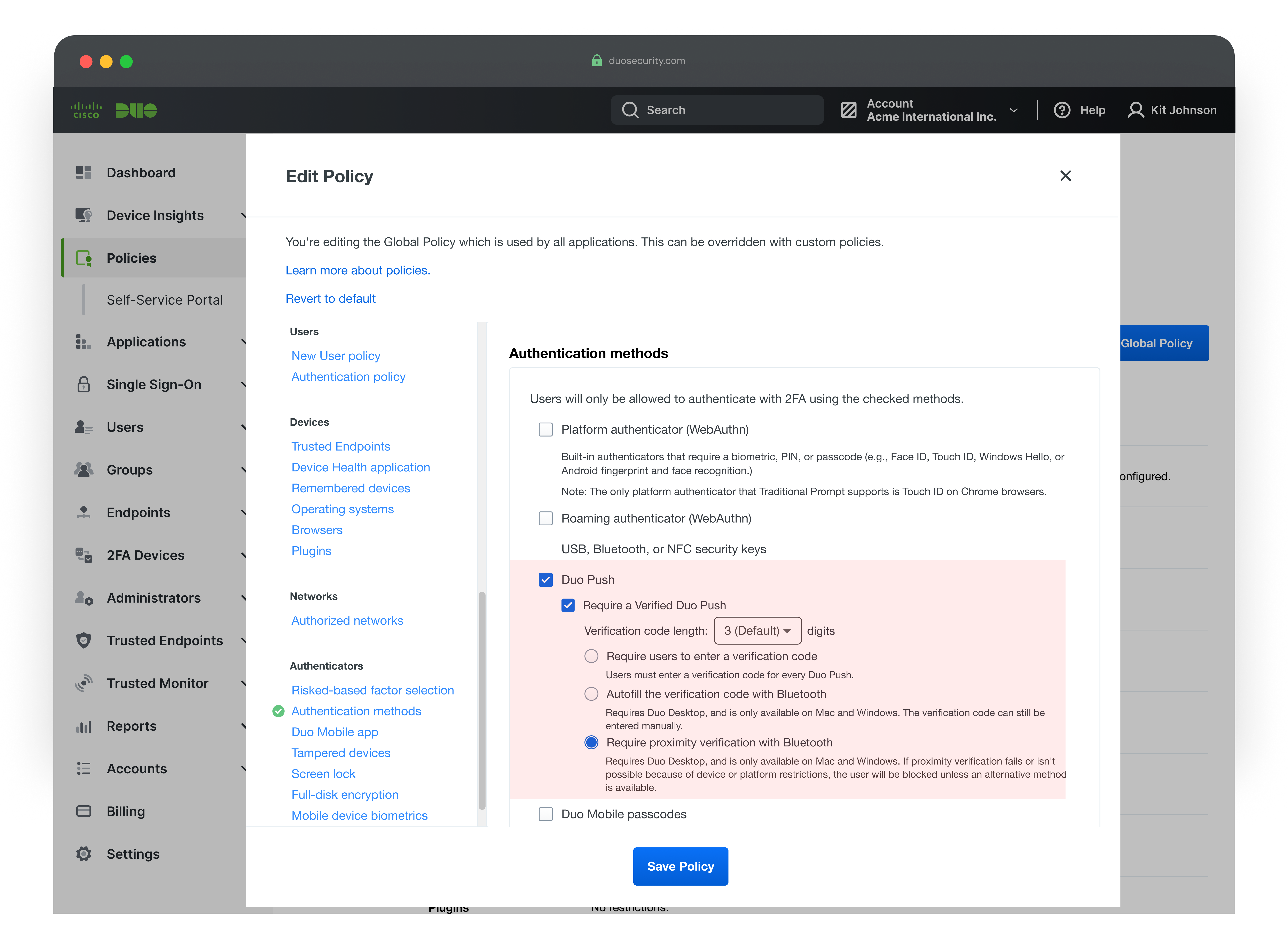
How Clear Is the Settings Configuration?
Lee’s user experience looks like a standard Duo Push screen, not a typical Verified Push, yet it’s configured under Verified Push settings. This could cause confusion since the visual doesn’t match the setting label.
Customer Insights
- Some customers expected users to see a Verified Push screen, while others saw the standard Duo Push screen and didn’t find it confusing or important.
- Organizations adopt phishing-resistant methods differently, often based on compliance rules or recent security issues.
- While most prefer strong phishing protection, they also want to avoid creating extra work for IT or confusing users.
- Clear tracking and logs are important so customers can confidently adjust policies without risking their organization.
Phase 2 Conclusions
- No changes were made to the settings configuration due to mixed customer feedback and technical limitations around nesting options under Verified Push. After several team discussions, we decided to focus on improving clarity through documentation.
- Bluetooth autofill is stable and has received positive feedback, but Proximity Verification adoption remains low during this phase since Bluetooth autofill was introduced earlier.
- Customers rely on Duo to stay current with security threats. While phishing-resistant methods can sometimes impact user experience, future compliance standards and evolving attacker tactics will likely drive wider adoption of stronger protections.
Phase 3
The initial phases went smoothly and successfully, with no major changes needed and a focus on ongoing refinement.

Goals:
- Improve the end-user experience with tweaks not addressed in earlier phases
- Enhance error handling for better reliability
- Improve tracking and reporting in authentication logs
- Collaborate with cross-functional teams to prepare for General Availability including documentation, marketing, and content design
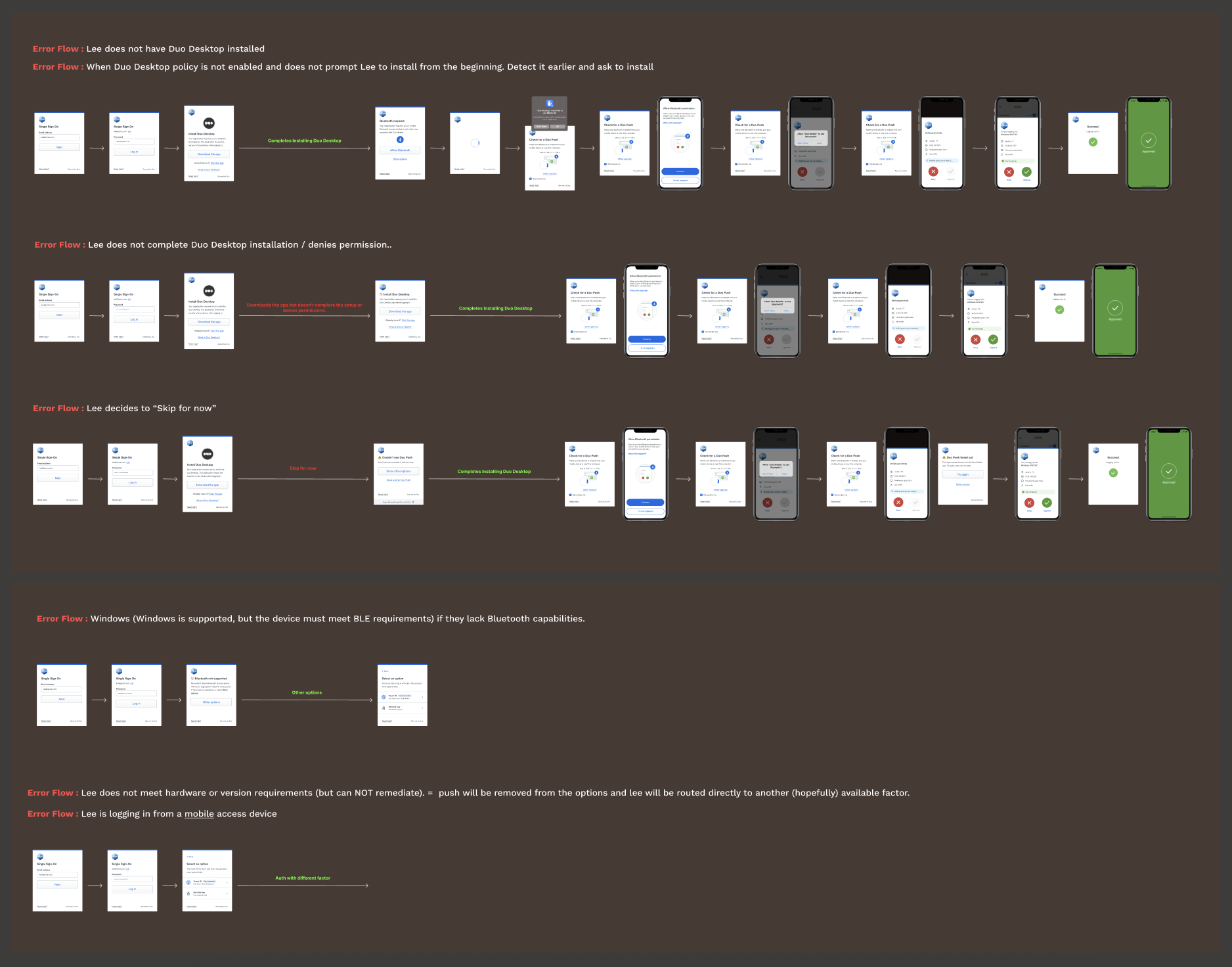
1) Handling Error States and Device Limitations
We reviewed all cases where Bluetooth might be unavailable and defined how users should recover versus when access is blocked. This included addressing platform support issues and adding prompt screens to guide users toward alternative actions.
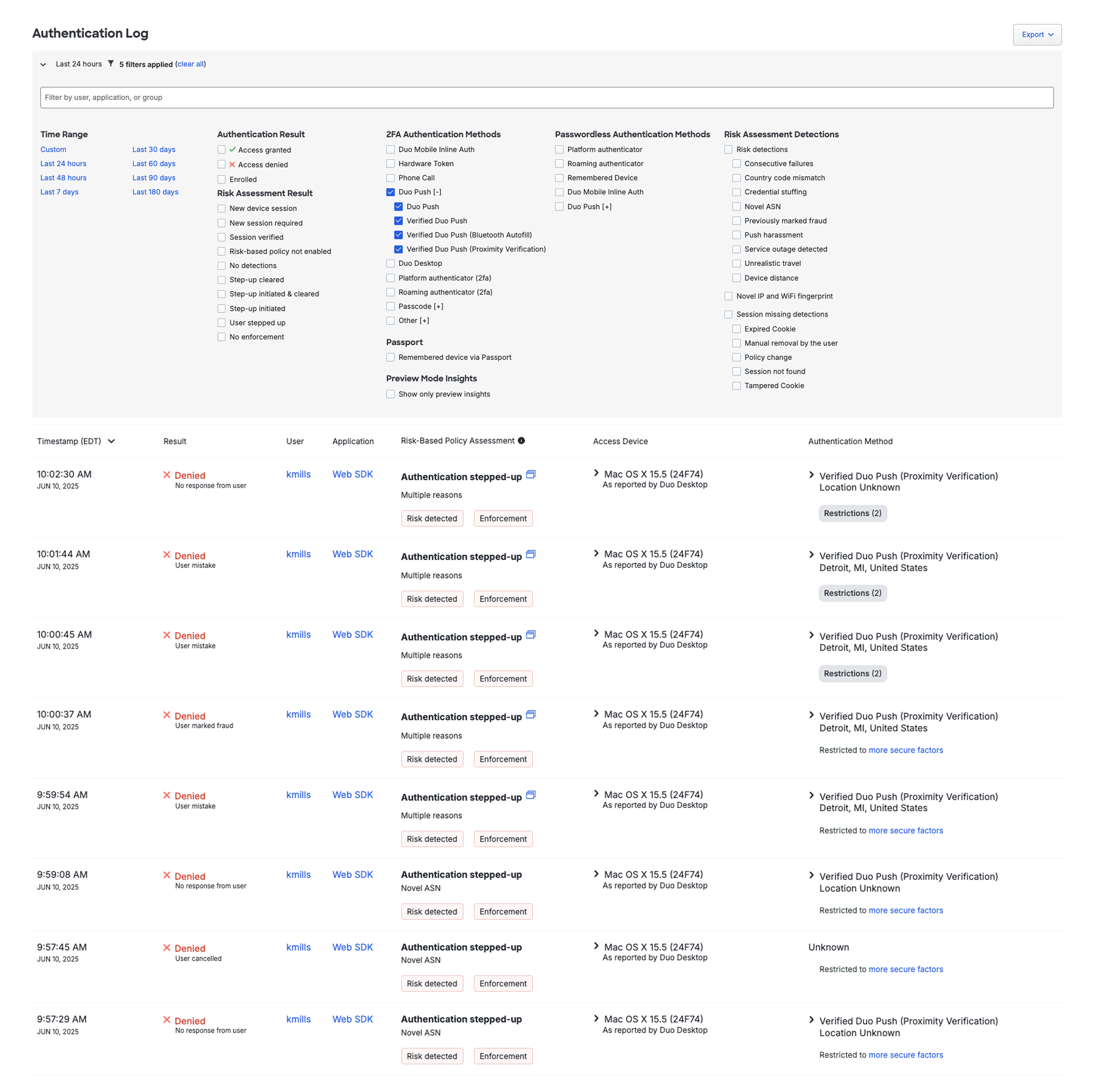
2) Authentication Logs and Tracking
From earlier phases, it was clear that IT administrators need detailed authentication logs showing which push requests were approved via Bluetooth versus other methods. We enhanced filtering options to align with the settings configuration and added clear indicators in the logs to highlight Bluetooth usage.
3) UI Improvements and Backlog Review
Proximity Verification can block users from moving forward, unlike Bluetooth Autofill, so we made small adjustments to existing prompt screens to offer alternative authentication methods. We also added Bluetooth indicators to illustrations and updated content on both device prompts and the Duo Mobile app to enhance clarity.
🎉 Official Launch
The Verified Duo Push with Bluetooth Autofill and Proximity Verification features became generally available in June 2025.
Identiverse Event
We presented our Verified Duo Push features with Bluetooth Autofill and Proximity Verification at the Identiverse conference, where they drew significant interest from attendees.
"This was the thing that we got the most interest from customers at our Identiverse booth"

"It's also awesome to be able to chat about this with a group of technical sellers who ask a ton of hard questions and to have absolutely no concerns about explaining what it is, how it's secure, how it compares to other FIDO2 solutions."
Looking Ahead:
We’re continuing to build on this work as proximity-based authentication becomes a core part of Duo’s long-term strategy.
- One of our largest customers shared that their auditor approved our solution as phishing-resistant, enabling a company-wide rollout.
- The Passwordless OS Logon feature uses Bluetooth-based proximity verification to ensure that Duo Push is only delivered when a user’s mobile device is physically near their workstation.
- As part of our broader effort to create a fully passwordless journey, we’re actively developing proximity verification to help establish trusted device-user binding.
Reflections
This section highlights what went well, where there was room to improve, and key takeaways from working on a complex, cross-platform authentication experience. It captures both the collaborative wins and the lessons that shaped my growth as a product designer.
✅ What Worked Well:
- Strong cross-functional collaboration between Product, Engineering, and Design fostered alignment and momentum.
- Frequent iteration loops and quick feedback cycles through customer calls helped us validate early assumptions and refine the solution.
- Having end-to-end ownership as a designer enabled deep problem understanding and solution continuity.
🛠️ Opportunities to Improve:
- Could have better clarified the behavioral and policy differences between Duo Push and Verified Push (VP) earlier, especially for strict enforcement use cases.
- Missed opportunity to proactively identify platform-level constraints between iOS and Android, which led to some late-stage adjustments.
🙏 Thankful For:
- Supportive and collaborative teammates who openly shared feedback and pushed the work forward.
- The opportunity to evolve this project from inception to implementation — and to experiment with different design and research processes along the way.
- Gaining exposure to complex security, mobile, and Bluetooth interaction patterns that deepened my product thinking.